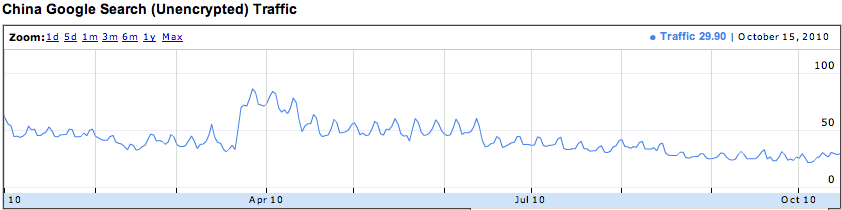
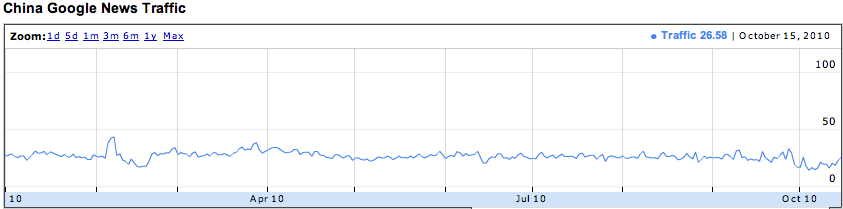
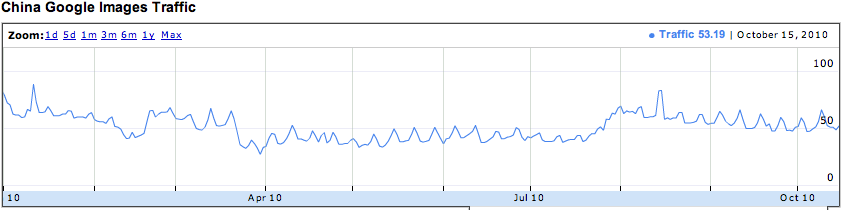
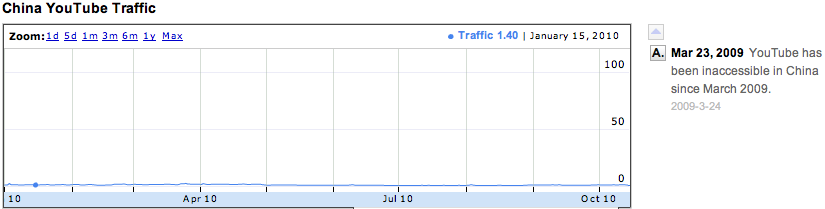
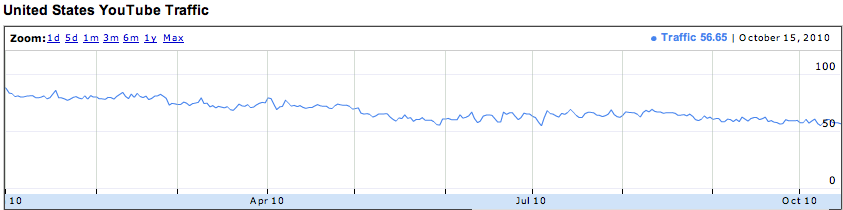
In a poorly executed attempt to control the flow of information to her citizens, China has implemented a national firewall. While the Great Wall was built to keep out foreign invaders, the Great Firewall attempts to keep out pornography, foreign culture, and international news. Politics aside, the Great Firewall of China is exceedingly inconvenient for travelers who want to stay in contact with friends and family, post their travels, upload photos, and keep abreast of international news. In the above diagrams, Google has demonstrated the amount of web content accessible in China as compared to an average of all nations. Below, you see US, which does much better at providing users access.
Access to services Google services from China as reported by Google Transparency
Fortunately, there is a simple two step process to circumvent the security measures China has put in place.
Step #1: Tunnel under the Great Firewall
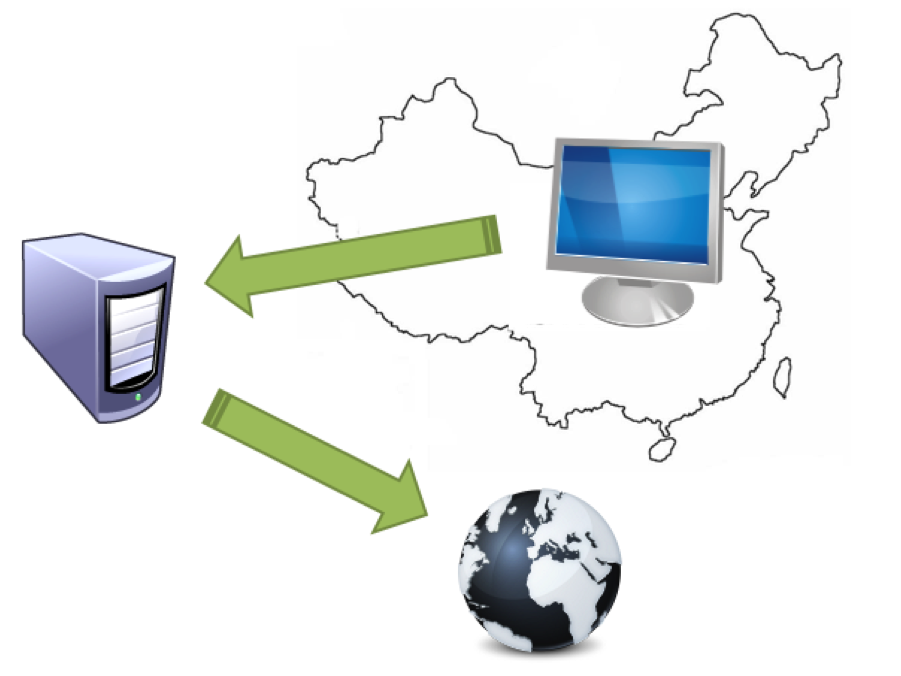
Like the Huns of the past, you need a way to get under, over, around, or through the Great Firewall of China. Fortunately, there is an easy and standard way that you can do this that the Chinese are unable to block. Basically, you will download special software to tunnel under the firewall, thereby providing a clear passage to send and receive web or any other Internet requests. For this covert operation, you have two options.
A tunnel uses a server outside of China to make web requests for you
Option 1: VPN Service
---- A VPN service reroutes all of your Internet traffic through an external server. The free services can be quite slow, may limit your bandwidth, and may work for only certain types of traffic (such as web browsing). The commercial services provide more flexibility and bandwidth, but will cost you a monthly fee. You must download, configure, and test the client before you leave for your trip because you will be unable to download it from China.
Option 2: Dedicated Proxy
---- The second option only works if you have your own dedicated server, such as a web server. The advantage of this is approach is that there are virtually no restrictions on bandwidth or content. Fortunately, The Road Forks has a dedicated virtual server hosted by
eboundhost.com
, which we highly recommend. If you already have a dedicated server, then this option will cost you nothing extra because you don't have to purchase a VPN client or service.
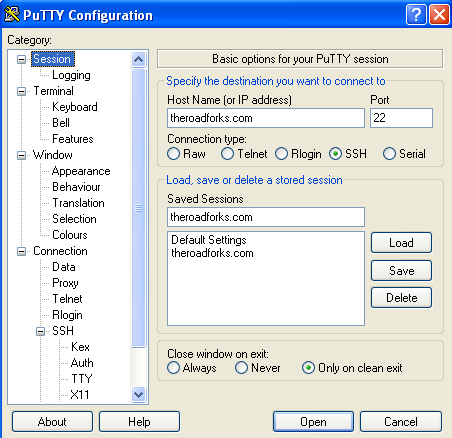
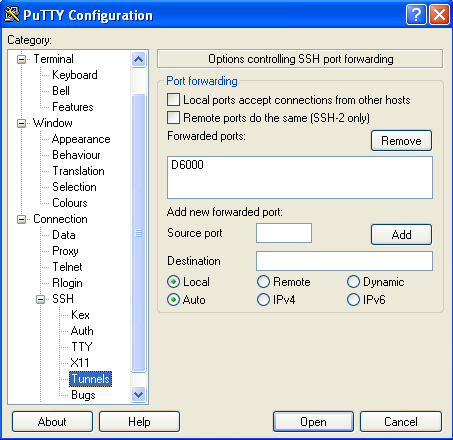
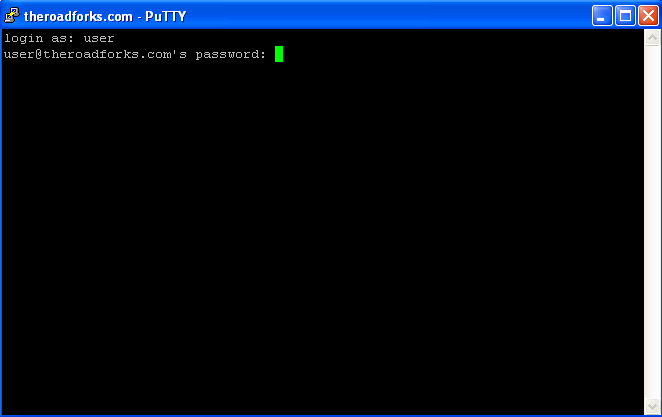
For PC machines: If you have a PC, download Putty , and configure the client to connect securely and open a proxy port locally. For some reason, I like port 6000. When you run the client, you have effectively setup a tunnel.
Setting up Putty connection; setting up Putty tunnel; connecting with Putty
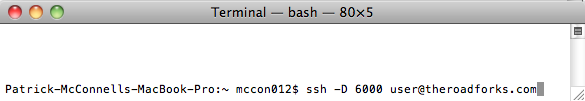
For Macs: If you have a Mac, believe it or not, you already have a tunneling client called Secure Shell. Open a command prompt with the Terminal app, which is found in your Applications folder. Type the ssh command with the -D flag, replacing “user” with your user name and theroadforks.com with your server name. See below for an example.
Command on a Mac to open a tunne l
Step #2: Lead your troops through the tunnel
Once you have your tunnel created, it is time to marshal your troops and lead them to victory over Chinese censorship. In this case, your troops consist of your software applications. Unfortunately, just because you have a tunnel, does not mean that your Internet requests will magically follow start flowing through them. Here, you again have two choices.
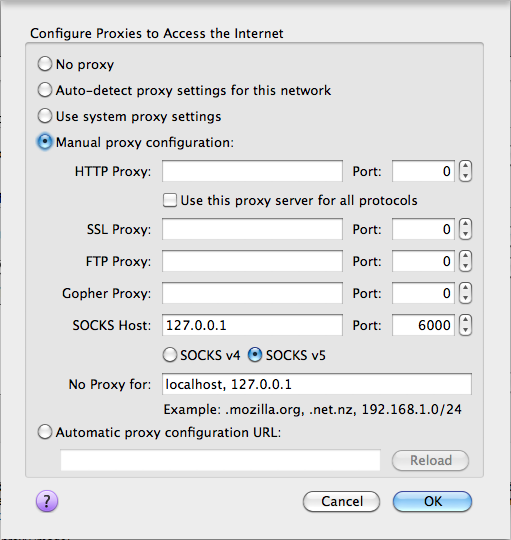
Option 1: Configured Web Browsers. The easiest way to do this is to open Firefox, go to Preferences->Advanced->Network and click the button to configure how Firefox connects to the Internet. Set Firefox to manual proxy settings, a SOCKS proxy, localhost for the server, and 6000 for the port. On a Mac, it looks like this:
Firefox configuration to use a local tunnel
Unfortunately, option one only work with web browsing using Firefox. For example, it will not let you watch movies since Adobe Flash does not use web browser proxy settings, and it will not let you use an instant messaging client. Do not forget to turn change your settings back when you don’t want to use the tunnel for browsing the web (that is, in your home country).
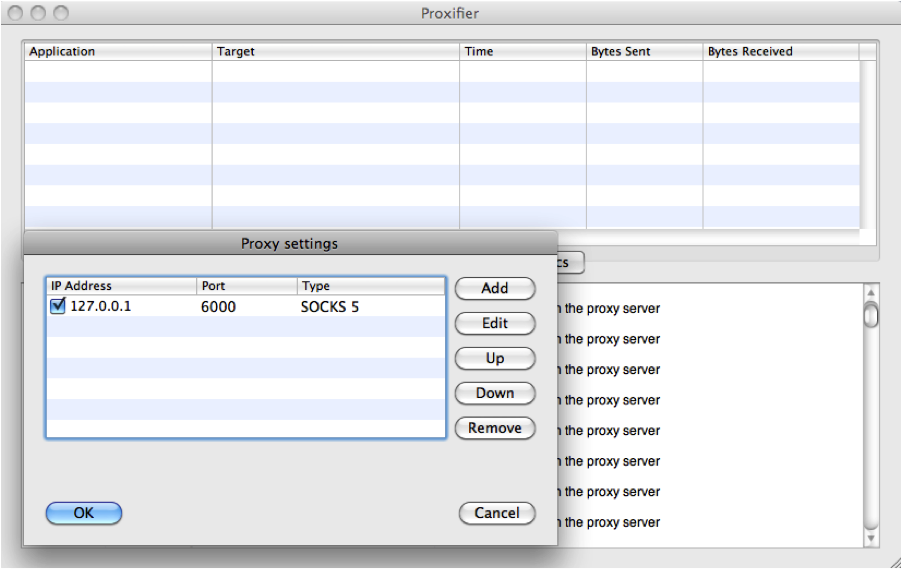
Proxifier configuration on a Mac to send all web requests through a tunnel
Option 2 - Commercial Proxy.
The second option is to purchase a commercial proxy tool that will intercept all of your Internet requests and send them through the tunnel. This is by far the most convenient method since it will work for all your software. We use Proxifier, which has a client for PC and Mac. You configure it much the same as a web browser. Just be sure to first build your tunnel before starting up the proxy. If things don’t seem to be working, close the proxy client, close the tunnel, check the Internet connection, start the tunnel, and start the proxy.
There are lots of ways to circumvent firewalls, but this mechanism seemed to us to be the most robust, easy, and convenient method.
Techie Tip: Use a public key to login without a password
Are you getting tired of typing your password in every time you get on the Internet and build your tunnel? There is one method that is universally accepted as a secure method to login to a server without typing in a password because it is based on the technology used to encrypt all the data that you are transmitted. In short, all data you send to a server is encrypted using the servers public key, and all data the server sends to you is encrypted using your public key. The only way to decrypt it is to use the private key, which is kept safe by the owner of the public key. You can ask the server to skip the password step for you by logging into the server and placing your public key is a specific place.
If you have a PC, follow the instructions at codelathe .
If you have a Mac, follow the instructions at remysharp .